A Stego' trend, and everyone is in on this one
Circa late '16, i was studying "PHP" lang (amongst others) and reviewing some case studies from a large infiltration and the widespread takeover of spanning several large scale providers that offered blogs, free pages, social accounts, etc. I'm leaving the names out but will give reference to the friendly name given: the infamous SEO Attacks. Stegonography is nothing new, I'm not reinventing the wheel here, but after over 3mos. of work last year and countless deep dives...I see this has gotten way out of hand for EVERY side that's using the technology. Just look at the wiki dumps from last week... After you read this and your still not convinced of the scale? Leave a comment, I can take you a bit deeper down the rabbit hole. I'm not a (conspiracy) theorist, I don't post a word unless I can back it up. I'm not a whistleblower, not considered good nor bad. Only da3m0n s3c, and this is FYI.
I combed through dozens of writeups, mostly by reputable nationally known Sec teams, including many personal accounts of their devastation and attempts at remediation and/or DR (disaster recovery). One thing quickly became evident, not a one was able to explain 'how'. There were article written for step by step recovery and changes that were being made to prevent any future attacks. However, those who are skilled within this area can immediately start to see the flaws/bugs in their fix. Even though the attempts made to fix the issues managed to band aid that type of attack, i saw several other ways to (workaround) this and exploit in various ways. Once you read through, you should easily see what I see. I originally decided against this writeup when I first complete my research, analysis and gathered the PoC's. I made this decision as it was 'in the dark' for most and quite sensitive, I didn't need any repercussions. Enough is out now, I have a good team and joined with many other sec's so it's time to open the findings to my viewers. It is still very sensitive and some names referencing those involved will be left out, trust me on this, it's for My better as well as to the readers. Enough jabber, let's begin...
If you hold any time in the field you know that it was just a matter of time before it was perfected. I will call this first vul 'Loaded Media'. I would hope everyone saw this coming: white, black, blue, red or purple teams. (Yes purple is gaining popularity quickly as a role in overseeing the Red Team's productivity and redirect as needed. A second set of eyes that are enough removed to not let emotions or stress cloud their judgement). It is the art of concealing executable code or payloads inside of all forms of media. I will focus on picture graphics in this post since the acl is much too large to go in-depth with all the catalysts. I will briefly mention others along the way though.
So, just to make this clear before the impending disclosure; loaded pix, video etc. can also make use of what's referred to as 'RFE' or 'RFI', acronyms for 'remote file execution' or 'inclusion'. There are methods for this within scripting languages of course, but one quick example comes to mind. I don't know if it has been fixed within html5 tags but are hard to obscure to a trained eye. Example: the '@' symbol, when coded correctly, has instructions to call a remote 'file' to perform whatever task. So what you would read as joe@example.com, can easily have Nothing to do with anything after @. That would actually be defined somewhere else in the page. please feel free to correct me if I'm wrong, but I don't believe this bug has been fixed in html5.
Let's move on to the pic issue, with a bit of backstory starting with what happened, how it took over and cross infected with unbelievable scale. I did happen across one a writeup from a skilled admin that cracked the case, identifying a Corrupt file common to most infected providers.
Earlier '16, a notable havker group had publicly stated their target and strategy to infect and take over every customer site from this provider, last checked they had well over 150k customers worldwide. They claimed that their role would then be as a zombie server to cross-contaminate everywhere, they stopped with that, obviously not going to give out their end game. I remembered this because I was actually impressed at their confidence and goals. I left some pieces out but this all in all had never been attempted. I know it was well beyond my musings until someone asked me to explain something and I read it closer. Wow!! Well, the time finally came and their bnet was mobilized/weaponized an it was a direct, successful hit. Keep in mind this was SEO oriented for phase1. Every banner, pop up, adware, click bait, everything targeted offshore gambling, porn and fake A/V (infection warning dialogues). People panicked at the ghost virus, both admins and clients alike bought the software which, you guessed it, didn't exist. Once the company started to release statements about the infection and remediation, everyone followed. Umm, nothing worked. Any code rewrites or reverts automatically pulled from their servers cache, where the corruption was hard coded to overwrite any changes. Even the cache would rewrite with infected, no one could do anything but watch as their sites got overrun. What they didn't know is this simple little code was placed in pictures uploaded to their CMS servers. The clients very content held the malcodes and infected other pics as they went through the client API into the CMS server. Many comparable providers saw similar scale infections. In the end it had various purposes hard coded, just one example was over 100 IP's that resolved to various overseas domains, many of which were ready to 'drive-by' inject their payload, get ranks or get paid. Along with all that, through some way, they ended up tarnishing the largest clean repo of images online... g00gle's. If I recall correctly the total amount corrupted before the sanitization started, was around 70% of their image db. Giving credit where due, they stated it was completely clean again within a couple days, and a fresh set of rules and sanitizers.
On to the ID and corrective measures. A blog admin from a small provider suffered the same fate. He happened to be an advanced PHP programmer. He took note that every provider that was infected was using PHP as a site builder, it manages graphic resizing without multiple images precreated and overall much more easy and efficient to code a dynamic page than just base html. After finding this commonality, he found the exploited file. The theme he happened to purchase to build his site had one file in common that was creating this havoc: timthumb.php. After making a statement and showing his PoC, all sites/providers immediately wiped everything as did each customer, it worked perfectly! It took some time to clean up the media on CMS server but they did get it clean. Lastly, there was heavy sanitizing rule sets put on the API's. Now normal Mr hacker can submit most of what he wants, the server will accept it unless it really chopped up bad, but they are much smarter now. The same pic uploaded, once viewed on the server, is download and/or checked and voila!, only the high quality pic remains, ALL code is stripped out. Hmm, nice work!! But unfortunately, not everyone has this technology on their API's. And those responsible for the SEO attack have been and gone. There a world of malicious people our there, all with their own intent, using many ways to get past these new constrainst or take advantage other ways and attempt to cross-infect/spawn.
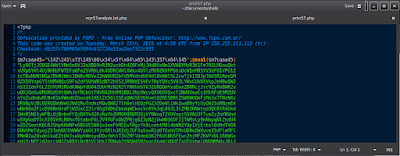
Linux systems, having the low level capabilities it does, along with. Sing a perfect environment to code in and comes with all the applicable langs you could want. I cannot divulge the lib package that gets loaded as a dependency for another tool. But with a special crafted use, it's command line can just about anything with any type pic extension, including burying code. Once created the code gets mangled but it's still able to auto execute every time it loads into a browser. There is no need to click on it. Your browser will automatically process everything within html tags and when it hits an img tag and starts to process the png, jpg or whatever, it will read through the data (to display the pic), beginning to process the RGB map and other info. But in example it finds a tag within that code opens to a '?' followed by 'php', It automatically calls the php interpreter to carry out any instructions between that and the '?' closing tag. Here's and example of a certain webshell code that would be buried on the EXIF headers as data.
There are now a few tools that will do the work for you and 'claim' to pass the most watchful API rules, I have not used them even to test validity but they are out there. I prefer hand processing with commands but to each his own.
In summary of the rambling; we've covered an evolution from a simple gif that can grad just about any visitor info you want, (best known for an IP logger), and append it to a text file on the host or other machine, to infecting servers and visitors alike with any range of malicious code, (with the payload embedded or calling an external script to execute on vic's machine.
As for Linux and it's role, it's only doing what it's supposed to do, it's people that manipulate and misuse tools meant for good. If you have been around for a while, you will know of which series and suites are good for this. Since I am not here to make a tuto for everyone, the names will stay in my head. G00gs is ur friend in this partnership. ; ) Every tool in Linux gives the user that open sourse, low level ability to design and make his OS and applications his own. Unlike a certain other where you are only able to customize the colors and all properties menus are fairly scant as well. uhmm, win... I must move on now, feel free to comment if you have questions or concerns.
And yes, I will post some clean samples (with a non-malious script, like arbitrary chars) and other PoC to show you! : )
Let it be known this has heavy usage in social media sites, incl. ytube. No room is safe, the better the pic, the more hits, views, shares and downloads. Exactly what they want. So what are some ways to tell if you have a loaded pic? It's best to have Linux and know the structure of pics, thoroughly. I prefer to use "ghex", a binary viewer/editor:
Available in most major distros with Gnome. See more info and screenshots at the official site [ here ]. Another command I like to use to just read the heaers in a file is the linux command "head" or is your distro has it available is "hexdump", although Ghex does pretty much the same. You can lso use the "strings" command to look for obvious signs of malformation; below is an example of another base64 encoding from strings command:
I combed through dozens of writeups, mostly by reputable nationally known Sec teams, including many personal accounts of their devastation and attempts at remediation and/or DR (disaster recovery). One thing quickly became evident, not a one was able to explain 'how'. There were article written for step by step recovery and changes that were being made to prevent any future attacks. However, those who are skilled within this area can immediately start to see the flaws/bugs in their fix. Even though the attempts made to fix the issues managed to band aid that type of attack, i saw several other ways to (workaround) this and exploit in various ways. Once you read through, you should easily see what I see. I originally decided against this writeup when I first complete my research, analysis and gathered the PoC's. I made this decision as it was 'in the dark' for most and quite sensitive, I didn't need any repercussions. Enough is out now, I have a good team and joined with many other sec's so it's time to open the findings to my viewers. It is still very sensitive and some names referencing those involved will be left out, trust me on this, it's for My better as well as to the readers. Enough jabber, let's begin...
If you hold any time in the field you know that it was just a matter of time before it was perfected. I will call this first vul 'Loaded Media'. I would hope everyone saw this coming: white, black, blue, red or purple teams. (Yes purple is gaining popularity quickly as a role in overseeing the Red Team's productivity and redirect as needed. A second set of eyes that are enough removed to not let emotions or stress cloud their judgement). It is the art of concealing executable code or payloads inside of all forms of media. I will focus on picture graphics in this post since the acl is much too large to go in-depth with all the catalysts. I will briefly mention others along the way though.
So, just to make this clear before the impending disclosure; loaded pix, video etc. can also make use of what's referred to as 'RFE' or 'RFI', acronyms for 'remote file execution' or 'inclusion'. There are methods for this within scripting languages of course, but one quick example comes to mind. I don't know if it has been fixed within html5 tags but are hard to obscure to a trained eye. Example: the '@' symbol, when coded correctly, has instructions to call a remote 'file' to perform whatever task. So what you would read as joe@example.com, can easily have Nothing to do with anything after @. That would actually be defined somewhere else in the page. please feel free to correct me if I'm wrong, but I don't believe this bug has been fixed in html5.
Let's move on to the pic issue, with a bit of backstory starting with what happened, how it took over and cross infected with unbelievable scale. I did happen across one a writeup from a skilled admin that cracked the case, identifying a Corrupt file common to most infected providers.
Earlier '16, a notable havker group had publicly stated their target and strategy to infect and take over every customer site from this provider, last checked they had well over 150k customers worldwide. They claimed that their role would then be as a zombie server to cross-contaminate everywhere, they stopped with that, obviously not going to give out their end game. I remembered this because I was actually impressed at their confidence and goals. I left some pieces out but this all in all had never been attempted. I know it was well beyond my musings until someone asked me to explain something and I read it closer. Wow!! Well, the time finally came and their bnet was mobilized/weaponized an it was a direct, successful hit. Keep in mind this was SEO oriented for phase1. Every banner, pop up, adware, click bait, everything targeted offshore gambling, porn and fake A/V (infection warning dialogues). People panicked at the ghost virus, both admins and clients alike bought the software which, you guessed it, didn't exist. Once the company started to release statements about the infection and remediation, everyone followed. Umm, nothing worked. Any code rewrites or reverts automatically pulled from their servers cache, where the corruption was hard coded to overwrite any changes. Even the cache would rewrite with infected, no one could do anything but watch as their sites got overrun. What they didn't know is this simple little code was placed in pictures uploaded to their CMS servers. The clients very content held the malcodes and infected other pics as they went through the client API into the CMS server. Many comparable providers saw similar scale infections. In the end it had various purposes hard coded, just one example was over 100 IP's that resolved to various overseas domains, many of which were ready to 'drive-by' inject their payload, get ranks or get paid. Along with all that, through some way, they ended up tarnishing the largest clean repo of images online... g00gle's. If I recall correctly the total amount corrupted before the sanitization started, was around 70% of their image db. Giving credit where due, they stated it was completely clean again within a couple days, and a fresh set of rules and sanitizers.
On to the ID and corrective measures. A blog admin from a small provider suffered the same fate. He happened to be an advanced PHP programmer. He took note that every provider that was infected was using PHP as a site builder, it manages graphic resizing without multiple images precreated and overall much more easy and efficient to code a dynamic page than just base html. After finding this commonality, he found the exploited file. The theme he happened to purchase to build his site had one file in common that was creating this havoc: timthumb.php. After making a statement and showing his PoC, all sites/providers immediately wiped everything as did each customer, it worked perfectly! It took some time to clean up the media on CMS server but they did get it clean. Lastly, there was heavy sanitizing rule sets put on the API's. Now normal Mr hacker can submit most of what he wants, the server will accept it unless it really chopped up bad, but they are much smarter now. The same pic uploaded, once viewed on the server, is download and/or checked and voila!, only the high quality pic remains, ALL code is stripped out. Hmm, nice work!! But unfortunately, not everyone has this technology on their API's. And those responsible for the SEO attack have been and gone. There a world of malicious people our there, all with their own intent, using many ways to get past these new constrainst or take advantage other ways and attempt to cross-infect/spawn.
Linux systems, having the low level capabilities it does, along with. Sing a perfect environment to code in and comes with all the applicable langs you could want. I cannot divulge the lib package that gets loaded as a dependency for another tool. But with a special crafted use, it's command line can just about anything with any type pic extension, including burying code. Once created the code gets mangled but it's still able to auto execute every time it loads into a browser. There is no need to click on it. Your browser will automatically process everything within html tags and when it hits an img tag and starts to process the png, jpg or whatever, it will read through the data (to display the pic), beginning to process the RGB map and other info. But in example it finds a tag within that code opens to a '?' followed by 'php', It automatically calls the php interpreter to carry out any instructions between that and the '?' closing tag. Here's and example of a certain webshell code that would be buried on the EXIF headers as data.
Note the highlighted string at the bottom. This tells us that at the end of this php, it will eval the results after a gzinflate, a str rot13 deocde and base64 decode. So what does this do for the attacker? Everytime a vic opens the file, they get a webshell and a nice shell of the remote that looks like so:
In summary of the rambling; we've covered an evolution from a simple gif that can grad just about any visitor info you want, (best known for an IP logger), and append it to a text file on the host or other machine, to infecting servers and visitors alike with any range of malicious code, (with the payload embedded or calling an external script to execute on vic's machine.
As for Linux and it's role, it's only doing what it's supposed to do, it's people that manipulate and misuse tools meant for good. If you have been around for a while, you will know of which series and suites are good for this. Since I am not here to make a tuto for everyone, the names will stay in my head. G00gs is ur friend in this partnership. ; ) Every tool in Linux gives the user that open sourse, low level ability to design and make his OS and applications his own. Unlike a certain other where you are only able to customize the colors and all properties menus are fairly scant as well. uhmm, win... I must move on now, feel free to comment if you have questions or concerns.
And yes, I will post some clean samples (with a non-malious script, like arbitrary chars) and other PoC to show you! : )
Let it be known this has heavy usage in social media sites, incl. ytube. No room is safe, the better the pic, the more hits, views, shares and downloads. Exactly what they want. So what are some ways to tell if you have a loaded pic? It's best to have Linux and know the structure of pics, thoroughly. I prefer to use "ghex", a binary viewer/editor:
 |
| Image courtesy of Ghex on gnome.org |
Which gives us this information on VT site, which isn't much but any oddity in here would throw some flags:
 |
| Image courtesy of VirusTotal/File Infomation tool. |
It is also important to remember that not at malicious code needs to be located in the header or EXIF information. Dependant of the image, there are 'dead zones' or chunks of space that contain no RGB data. Again, in these cases a hex viewer would be ideal. However, there are a couple online tools that can process pictures. It's useful tools are geared more for a trained eye on what to look for. I prefer one over the other sinse it has a much more scalable view and measures one very important with much more accuracy than the other; the ELA, or Error Level Analysis. It's a tough explanation but I'll give you a quick lesson. (BTW there is lesson steps and different test on my top pick, just click around and you'll find them. So Practice. Here is the crash course for now: under ELA, white and close to white should be black, and pure black should be white. Everything in between should be of some contrast colors, with the contrast level dependant on the shit from white. Get it? That's fine if you have to read that a couple of times. This normally is used for detecting original, unmodified photos. However, you can use these rules and incorporate some others to give a fairly good determination if there is code buried within the image. I will get to that in a minute. I first want to show you two images, neither are loaded but the first shows the image has been altered, the second is good. I will explain each.
 |
| fig 1. Bad ELA/Altered photo |
 |
| fig 2. Good ELA/photo |
Fig. 1 Is originally a pretty dark photo, except for a couple spots. A white light in the treeline is black so that is ok, The white smoke from the white jay in his hand are showing white, this is a sign of tampering as well as his hoodie. It is dark grey with some lighter spots, in ELA the coloring you see above is backwards, which again shows a possible color tamering. All this is too unfirm for a sloppy embedded code. Again, I'll explain what you need to look for after I briefly cover the second image.
Fig. 2 Is a perfectly fitting ELA. It is for the most part a geo'd IP with map output using satellite. Notice the white is black, black is white and EVERY other color has a certain level of contrast off from white and is therefore shown by color(s). Perfect!
There are two good sites that can give you a wealth of info on the pic outside of wheat VT can deliver. My top pic is first being Fotoforensics and next is Imageforensic. Take a look around the first one, it even has a built in malware scanner, (how well it works, i don't know, but it's there.
Alright, now some red flag signs that you have come across a loaded image file. It may be easiest to give you a good example from my analysis, unfortunately I could not save the asset and wasn't near my Linux box to take it apart. Here's what I saw that all pointed to a bad embeddded code by a bad tool, a skid or someone else that didn't expect anyone like me would analyze it. First flag, it was portrayed as just being taken by cell phone, NO. The pixels came back at .312 or so, this mean one of two things; either it was taken with the quality of a CCTV cam or it has been altered by a image manipulation app like P-shop or GIMP and uploaded to the internet which kills the pixels. Straight phone cam shot whether screenshot or photo should be well ove 6 megapixel. This was very pixelated. Second flag, most cell phones will shoot a 4:3 or some cases, 16:9. This was 10px short of a 4:3 which means it had something trimmed off. There was nothing top or bottom that should've needed sanitizing. Third flag, you will learn this definition soon enough but the rainbow effects where everywhere, (even everywhere they shouldn't be). The white thin clouds were contrasted and the big blue sky was black. Bad. The last flag showed me exactly where he tampered with the image and placed the code. There was a rainbow effect scaling around the entire sky just before the clouds, a beliberate empty void of blackness where there should've been a lot of color contrasting. This tells me that the color was dropped out from inside those rainbow (cut marks). This would've given the coder ample space to inset the code without manipulating much of the outward look of the pick. If I do come across another one, (safely). I prmise I'll update this post to show you just how bad an ELA can get and how much you can learn from them online without compromising your 'puter.
Last two things I forgot to mention on the analysis: a large amount of 'extra' binary data in the png or entropy. Both red flags during an online analysis.
Enjoy your new found paranoia folks!! I hate to say it but they are everywhere in social media. Not just havkers anymore. Big business is paying dearly for this type of hidden code. Targeted marking, BigData count on stuff like this and it all sells for big money! Ooops, I forgot one group, oh well, they are creating enough media coverage on their own. Hehe, I don't need to dropo any names... My advice, limit your surfing, any home feeds and don't click on SHIZ unless you can safely handle it and analyze without opening. Ohh, and just another tip, a reminder of sorts from an earlier post. Don't forget about the 'hidden' gifs with buried code. The get put in sites, banner ads, emails, just about anywhere you can think but they have maybe a 1px dimension, transparent properties, hidden or both. Be vigilent on that source code! GL...
Cheers!!
'd_c0'



Comments
Post a Comment