Decryption and Analysis of a "Shell" Backdoor
UPDATE [l]: shortly after finishing this post, I had decided to do a couple scans of the raw code. The results returned several Shell Trojan variants, and doing some permanent damage to windows systems. Reports available at ] VirusTotal ] and [ Malwr ]. Thanks to both services for the great results. It attempted network connx with the original url, not surprise from a webshell, IMO, only a bit strange that the likely 0wn/Op would keep such a trophy case in the wild like that? I mean really??. I would've expected an http request or few since nce that's who was hosting the assets but the requests were made to connect to "Hostthshellcode and then starts the endless streaming of the v1c's data and a continual stream of fresh code for the mal to swap out. This only confirmed the feeling I had about the src code. Multiple langs being used, illogical syntax and it's all just mixed together... if anyone can answer how this can support the back and forth exec using Perl, HTML (CSS|Js), Bash, C and 'Shell' script and still be platform agnostic (??) as several dangerous variants are from the start. I would love to hear how this was accomplished. It just goes against programming 101, I know some syntax can be seemingly interchangeable, until you reach a quite advanced knowledge of theory and can apply those skills effectively in the field. ;)
UPDATE [ll]: I just wanted to provide you with a more thorough status on this site/malz. After a thorough analysis, here is some interesting data points I returned:
Site: privshells.com
IP: 66.175.58.98
CO: Turkey
Status: blacklisted / UP
Code ( in page ) contains:
Troj.Asp-C, Troj.ASPX-B, Troj.Aspdoor-B:
( as reported by Sophos ).
And compiled reports from the following services:
[ VT ]~] Sucuri [~ ~] Quterra [~ ~] Yandex [~
###===========###
I had no idea when I started this project yesterday, that it would be something I would publish. But this one was unique. There are not many occasions that you will come across this type of file, but when you do, you will thank me for this tuto for two reasons. (1) Whatever, wherever or however you can into possession of this isn't my business, but be assured it IS malicious. (2) What little information is available about this unique format of executable PHP, we do know it's a custom encryption that uses a base64 style encoding. By custom, I am referring to three anomalies that stood out for me:
1. The encoding process requires a user defined cipher key which gives every encryption a unique algorithm, also required for decryption using the same resource.
2. The defined use of custom
3. PHP's ability to not only decrypt this but also, at least in this case, can read and exec multiple langs. You will see in the following code snippet photos, it uncovered the use of six languages within that string. Yes, it took six manual rounds to be able to fully decode everything...
Ok, let me set the stage here. This was an analysis of a popular shell, the r57. I have several others i have taken apart and analyzed, there are some distinct differences as the features between each vary. I am using this one for purposes of example, and covering the functionality as seen by the source code and do not endorse the use of any shells or other means of backdoor creation, reverse shell (rShell) or other type bindings. I assume most of you understand what a shell is and how it works. Yes? Good, that means you read the preceding sentences, ;). I will discuss some of it's functionality and processes that are apparent from walking code... the numerous intermingled syntax varied langs. The reason for this is to show what can be, and and often is behind these complex obfuscations. Somebody worked incredibly hard and put a lot of thought into this shell.
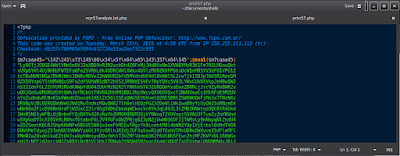
The issue: a proprietary method to encode any malicious source and have it remain executable. This has been gaining in popularity within different areas, and from the endless searching yesterday, it doesn't seem like too many people have a full handle on it's decryption. Let's take a look into the process I used to break the FOPO encoding, and take a look inside too these files can be hiding. Here is the distinctive header and the beginning of a dangerous string of almost 60,000 chars.
f you come across this, I would recommend submitting it to an appropriate sec team for analysis. But for those that would like to get this apart by themselves without tearing out hair, lets continue. I will not endorse this encryption so I will not link to the site. However, I think if you clicked to view the fullscreen pic you will likely see it yourself, and yes, their site is up. Just be warned it's not too good at keeping it's secrets anymore. I did find a couple resources online to get this job done, it may have taken some time but definitely better than by hand. Some methods you may find online are talking about doing it manually, don't waste your time yet. I highly doubt it would work in many situations. I have also heard that Python has a program that will take it apart in just a few seconds, there was no proof shown of the success, so I will not mention it, it can be g00g'd fairly quick if you feel the need to try it. The effectiveness is solely dependent on the file, it's complexity and size. There is a very good online decoder, I believe it's source is available for download as well. I found the Decode Fopo v1.2 software, and online version of the decoder here ~] lombokcyber [~. As you will see, it works quite well. Thanks for the great implement.!
Again great tool but it only took me so far as you will see, it didn't reach several layers. Below is a shot of the decode, you can see that there was going to be some more work as the encoding starts back up. It's makes me laugh how none of this code in these giant blocks sould logically functioned with each other... but, it just does. Please don't bother with trying to read the code, the screenshots show examples and not the entire program. We will get into the behaviors of each, and the overall program later. Trust me, there's not much pleasant about any of it. This is what we do though so nothing of a surprise here, a typical pwn with a lot of manual work written into it's functions. You don't want this on your server or localhost. Sysadmin or not, I am just giving a heads up to anyone that may not be familiar with this type of havk, it's not very pleasant. Anyway, moving on, let's see where it stopped...
You can see that we made it to
And another requisite shot of the code (snippet) below... Oh, you though I was going to give a full code disclosure? Haha no... not ever... sorry. ;)
This one isn't doing much outside what it's name already implies. Creating sockets, ip addrs, binding ports, new root user and pw, setting up all the configs and listeners started. I am decoding the string
Similar things running in this program as well. Fork, bind, set, use/reuse, connect, listen and requesting cmd when needed, some things set to run as a daemon. That's about all that's needed for that. Next we're going into the
I'm going to move through these next couple as well. Similar to the others, it is doing it's work on setting up pipes for connect and data handling. Here are shots of
The last round I had returned a Perl program that is dealing with header manipulation and other transactional type obscurement. This is actually a good segue into what is actually the beginning. An interesting fact when I was doing rounds by hand, I noticed in the fist round that the start of the program is located somewhere in the last half of that string. Interesting logic, it's like C trying to start a program without
So what has all been happening with the rest of the code? It's getting it's GUX from html and is actually quite busy running a continual fs siphon (and other things) within that. Here is a quick shot, but I should really step through that code because it has purpose behind the scenes..
This is where it start to get real intrusive. Bear in mind this is only one persons shell. What other extra functions any other shell has is up to their coder. This one, for starters, is creating symlinks on localhost to all the critical dirs within the remote fs. It also searches for all config files containing info it wants and reads the info or overwrites/appends as needed. I do see quite a bit of
Last thing I will point out as I think I've shown enough PoC; is that there are is a large amount of queries and overwrites appends to any file that may be exploited; system files, software, configs, security, modules, persistence and a lot more. I'll just say it's very busy for many different but apparent reasons. I have gone into the behavior some because it's relevant in showing a proof of concept. There are some that would look at the encoded file and not have much suspicion, however, this is just what can be expected hiding if you come across this encoding ... So I won't get much more explicit on behavior than that. There isn't anything happening here that I haven't seen before, but definitely one I will never forget due to how it all works. I have a good handle on PHP, and the others I found being used. I cannot explain how all the different code is executed.
I promised a list of online encoders/decoders other than the one mentioned earlier. Here you go..:
[+] base64decode the only site that can resolve base64 image encoding.
[+] tools4noobs tools for many different php functions.
[+] perishablepress so many choices.!!
[+] ddecode a multi purpose analyzer, built for WP admins.
[+] unphp another adaptative, multi functional php deobfuscator.
[+] online code generator an endless selection of decoders.
[+] codebeautify the most thorough!! 100 unique conversions.
[+] manytools a vast toolsuite of encoders of every type.
[+] crypo the best for last. very dark and obscure encodings, anything.! I thought I knew them all...
That's going to be it for now. I will cover more tools in a later post. ;) Cheers.
- d_c0
UPDATE [ll]: I just wanted to provide you with a more thorough status on this site/malz. After a thorough analysis, here is some interesting data points I returned:
Site: privshells.com
IP: 66.175.58.98
CO: Turkey
Status: blacklisted / UP
Code ( in page ) contains:
Troj.Asp-C, Troj.ASPX-B, Troj.Aspdoor-B:
( as reported by Sophos ).
And compiled reports from the following services:
[ VT ]~] Sucuri [~ ~] Quterra [~ ~] Yandex [~
###===========###
I had no idea when I started this project yesterday, that it would be something I would publish. But this one was unique. There are not many occasions that you will come across this type of file, but when you do, you will thank me for this tuto for two reasons. (1) Whatever, wherever or however you can into possession of this isn't my business, but be assured it IS malicious. (2) What little information is available about this unique format of executable PHP, we do know it's a custom encryption that uses a base64 style encoding. By custom, I am referring to three anomalies that stood out for me:
1. The encoding process requires a user defined cipher key which gives every encryption a unique algorithm, also required for decryption using the same resource.
2. The defined use of custom
$myfunction=" "; also there is no decoding functions being passed to interpreter for decoding, like the following: gzinflate(str_rot13(base64(" ")));.3. PHP's ability to not only decrypt this but also, at least in this case, can read and exec multiple langs. You will see in the following code snippet photos, it uncovered the use of six languages within that string. Yes, it took six manual rounds to be able to fully decode everything...
Ok, let me set the stage here. This was an analysis of a popular shell, the r57. I have several others i have taken apart and analyzed, there are some distinct differences as the features between each vary. I am using this one for purposes of example, and covering the functionality as seen by the source code and do not endorse the use of any shells or other means of backdoor creation, reverse shell (rShell) or other type bindings. I assume most of you understand what a shell is and how it works. Yes? Good, that means you read the preceding sentences, ;). I will discuss some of it's functionality and processes that are apparent from walking code... the numerous intermingled syntax varied langs. The reason for this is to show what can be, and and often is behind these complex obfuscations. Somebody worked incredibly hard and put a lot of thought into this shell.
The issue: a proprietary method to encode any malicious source and have it remain executable. This has been gaining in popularity within different areas, and from the endless searching yesterday, it doesn't seem like too many people have a full handle on it's decryption. Let's take a look into the process I used to break the FOPO encoding, and take a look inside too these files can be hiding. Here is the distinctive header and the beginning of a dangerous string of almost 60,000 chars.
f you come across this, I would recommend submitting it to an appropriate sec team for analysis. But for those that would like to get this apart by themselves without tearing out hair, lets continue. I will not endorse this encryption so I will not link to the site. However, I think if you clicked to view the fullscreen pic you will likely see it yourself, and yes, their site is up. Just be warned it's not too good at keeping it's secrets anymore. I did find a couple resources online to get this job done, it may have taken some time but definitely better than by hand. Some methods you may find online are talking about doing it manually, don't waste your time yet. I highly doubt it would work in many situations. I have also heard that Python has a program that will take it apart in just a few seconds, there was no proof shown of the success, so I will not mention it, it can be g00g'd fairly quick if you feel the need to try it. The effectiveness is solely dependent on the file, it's complexity and size. There is a very good online decoder, I believe it's source is available for download as well. I found the Decode Fopo v1.2 software, and online version of the decoder here ~] lombokcyber [~. As you will see, it works quite well. Thanks for the great implement.!
Again great tool but it only took me so far as you will see, it didn't reach several layers. Below is a shot of the decode, you can see that there was going to be some more work as the encoding starts back up. It's makes me laugh how none of this code in these giant blocks sould logically functioned with each other... but, it just does. Please don't bother with trying to read the code, the screenshots show examples and not the entire program. We will get into the behaviors of each, and the overall program later. Trust me, there's not much pleasant about any of it. This is what we do though so nothing of a surprise here, a typical pwn with a lot of manual work written into it's functions. You don't want this on your server or localhost. Sysadmin or not, I am just giving a heads up to anyone that may not be familiar with this type of havk, it's not very pleasant. Anyway, moving on, let's see where it stopped...
You can see that we made it to
$port_bind_bd_c=" "; and for all intensive purposes, I would say that this is likely short to bind port 'x' for the backdoor remote access, written in C...? Maybe... I need to figure out how to decode the rest of these first. There's several online tools for encoding/decoding, and no shortage of base64 either. I will provide a list of reputable enc/dec at the bottom, each has it's own niche for decoding certain files. I have to say the bottom one bottom one is a little 'dark', however, they have about 25 or more options and so rare, I hadn't heard of 90% of their options. That's why I can't recommend one over the other, each has done well in various obsfucation. It's a matter of what works with the code you have at the time... but the only one that worked with these embedded strings is ] base64decode.org [. Let's take a look quick look at the code and then I'll describe the behavior of each based on the code as written. Hmm, looks like C headers to me.And another requisite shot of the code (snippet) below... Oh, you though I was going to give a full code disclosure? Haha no... not ever... sorry. ;)
This one isn't doing much outside what it's name already implies. Creating sockets, ip addrs, binding ports, new root user and pw, setting up all the configs and listeners started. I am decoding the string
$port_bind_bd_pl=" "; may be a safe assumption that we are going to see is similar but in Perl...? Yup, looks like out first line contains a shebang for Perl...Similar things running in this program as well. Fork, bind, set, use/reuse, connect, listen and requesting cmd when needed, some things set to run as a daemon. That's about all that's needed for that. Next we're going into the
$back_connect_c=" "; functions... you guessed it too, one for C and one for Perl. Here they are respectively...I'm going to move through these next couple as well. Similar to the others, it is doing it's work on setting up pipes for connect and data handling. Here are shots of
$bd_pipe_pl=" "; configs, the first in C and then the redundant Perl scripts.The last round I had returned a Perl program that is dealing with header manipulation and other transactional type obscurement. This is actually a good segue into what is actually the beginning. An interesting fact when I was doing rounds by hand, I noticed in the fist round that the start of the program is located somewhere in the last half of that string. Interesting logic, it's like C trying to start a program without
int main([]) , lol..So what has all been happening with the rest of the code? It's getting it's GUX from html and is actually quite busy running a continual fs siphon (and other things) within that. Here is a quick shot, but I should really step through that code because it has purpose behind the scenes..
This is where it start to get real intrusive. Bear in mind this is only one persons shell. What other extra functions any other shell has is up to their coder. This one, for starters, is creating symlinks on localhost to all the critical dirs within the remote fs. It also searches for all config files containing info it wants and reads the info or overwrites/appends as needed. I do see quite a bit of
$ curl and $ wget , those have their purpose in pwning. If you are a sysadmin or have been around linux for any period of time, I think you are aware what a crafted $ sed or $ curl could do with all your conf files. This data is then streamed off via pipe or ftp, UDP or other protocol it is told to use. Many of the other processes from earlier where started as daemons so the user is guaranteed not to drop any connect. Although these shells don't leave much of a footprint by design, this one audits of all the log files for trace entries and will either scrub the entries or even symlink to some of the server's logfiles as well. It monitors system resources closely to keep remote up an stable and checks to make sure no oom's are being executed, and your system stays up for 'use'. There is also a lot of system infos being gathered and viewed with $ cat command. If you view the full size pic above, you will notice ALL the Bash cmds and what they are doing. Think of the infos they get from just this: locate ".conf" >>/tmp/grep.txt '=>' cat /tmp/grep.txt read and can be siphoned off whenever. If you read the whole thing, it is getting every important document from a Linux system. just a couple more noteworthy details for now, I could spend hours listing everything it's doing. Albeit very interesting to see the total invasion, this isn't a tuto on writing backdoors, rshells, data-miners or any other exploits, I see many in the source. Yes, we do a lot of reversing but this is about dealing with a special encoding/encryption and how to decode it and likely find some serious malice. (yes, I know encoding and encryption are different). This is clearly a case when both terms are appropriate though.Last thing I will point out as I think I've shown enough PoC; is that there are is a large amount of queries and overwrites appends to any file that may be exploited; system files, software, configs, security, modules, persistence and a lot more. I'll just say it's very busy for many different but apparent reasons. I have gone into the behavior some because it's relevant in showing a proof of concept. There are some that would look at the encoded file and not have much suspicion, however, this is just what can be expected hiding if you come across this encoding ... So I won't get much more explicit on behavior than that. There isn't anything happening here that I haven't seen before, but definitely one I will never forget due to how it all works. I have a good handle on PHP, and the others I found being used. I cannot explain how all the different code is executed.
I promised a list of online encoders/decoders other than the one mentioned earlier. Here you go..:
[+] base64decode the only site that can resolve base64 image encoding.
[+] tools4noobs tools for many different php functions.
[+] perishablepress so many choices.!!
[+] ddecode a multi purpose analyzer, built for WP admins.
[+] unphp another adaptative, multi functional php deobfuscator.
[+] online code generator an endless selection of decoders.
[+] codebeautify the most thorough!! 100 unique conversions.
[+] manytools a vast toolsuite of encoders of every type.
[+] crypo the best for last. very dark and obscure encodings, anything.! I thought I knew them all...
That's going to be it for now. I will cover more tools in a later post. ;) Cheers.
- d_c0










Comments
Post a Comment