New 2017 Shellcode | Titles -- Link Direct to Code
I've compiled a list of the most current shellcodes and linked each directly to their raw code. I am providing this list for analytical purpose to those that may be interested. Enjoy and use responsibly...
Windows x64 password protected bind shellcode.
Windows x64 CreateRemoteThread() DLL injection shellcode.
Linux/x86_x64 mkdir("ajit", 755) shellcode.
Linux/x86_64 shellcode that binds to TCP/5600.
Linux/x86_64 execve /bin/sh shellcode.
Linux multi/dual mode execve("/bin/sh", NULL, 0) shellcode.
Linux multi/dual mode reverse shell shellcode.
Linux/x86 reverse TCP alphanumeric staged shellcode.
Linux dual / multi mode bind shell shellcode.
Windows x86 protect process shellcode.
Linux reverse shell shellcode.
Linux x86-64 egghunter shellcode.
Linux x86_64 random listener
Windows x86 executable directory search shellcode.
RSA Asymmetric Polymorphic Shellcode.
Windows x86 reverse TCP staged alphanumeric shellcode.
Linux x86_64 polymorphic setuid(0) and execve(/bin/sh) shellcode.
Linux x86_64 polymorphic flush iptables shellcode.
Linux x86_64 polymorphic netcat reverse shell shellcode.
Linux x86_64 netcat reverse shell shellcode.
Windows x86 hide console window shellcode.
Linux/x86 file reader shellcode.
Art of Anti Detection 3 - Shellcode Alchemy.
This shellcode uses CreateFile and tries to read a non existing network path. You can use tools such as Responder to capture NetNTLM hashes. The shellcode can be modified to steal hashes over internet. SMBRelay attacks can also be performed.
This list was compiled from 01/01/2017 thru 03/23/2017.
Data and code courtesy of Packetstormsecurity. Thank you!
Cheers,
'r3v
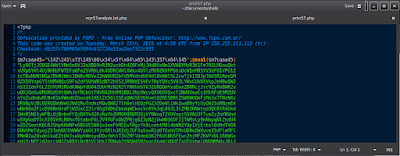
UPDATE: since we are somewhat on topic for creating backdoors using reverse shell. I went on a hunt to find a SINGLE image. A Security Er for a well known infosec team found a backdoor on a system that was currently still in use. He managed to get the rsh program used during the attackers session on local. However, due to the scale and capabilities he was likely using it to manage a smaller bnet. Anyway, I think it was written in BASH but I could be wrong. Thankfully I didn't have to search long and found the original screenshot of the tool, it's quite impressive as ur's expansive usage as to where normally u will have a small terminal type window to and make your way through the server, but...whatever. Here's a screenshot of the rsh.
Windows x64 CreateRemoteThread() DLL injection shellcode.
Linux/x86_x64 mkdir("ajit", 755) shellcode.
Linux/x86_64 shellcode that binds to TCP/5600.
Linux/x86_64 execve /bin/sh shellcode.
Linux multi/dual mode execve("/bin/sh", NULL, 0) shellcode.
Linux multi/dual mode reverse shell shellcode.
Linux/x86 reverse TCP alphanumeric staged shellcode.
Linux dual / multi mode bind shell shellcode.
Windows x86 protect process shellcode.
Linux reverse shell shellcode.
Linux x86-64 egghunter shellcode.
Linux x86_64 random listener
Windows x86 executable directory search shellcode.
RSA Asymmetric Polymorphic Shellcode.
Windows x86 reverse TCP staged alphanumeric shellcode.
Linux x86_64 polymorphic setuid(0) and execve(/bin/sh) shellcode.
Linux x86_64 polymorphic flush iptables shellcode.
Linux x86_64 polymorphic netcat reverse shell shellcode.
Linux x86_64 netcat reverse shell shellcode.
Windows x86 hide console window shellcode.
Linux/x86 file reader shellcode.
Art of Anti Detection 3 - Shellcode Alchemy.
This shellcode uses CreateFile and tries to read a non existing network path. You can use tools such as Responder to capture NetNTLM hashes. The shellcode can be modified to steal hashes over internet. SMBRelay attacks can also be performed.
This list was compiled from 01/01/2017 thru 03/23/2017.
Data and code courtesy of Packetstormsecurity. Thank you!
Cheers,
'r3v
UPDATE: since we are somewhat on topic for creating backdoors using reverse shell. I went on a hunt to find a SINGLE image. A Security Er for a well known infosec team found a backdoor on a system that was currently still in use. He managed to get the rsh program used during the attackers session on local. However, due to the scale and capabilities he was likely using it to manage a smaller bnet. Anyway, I think it was written in BASH but I could be wrong. Thankfully I didn't have to search long and found the original screenshot of the tool, it's quite impressive as ur's expansive usage as to where normally u will have a small terminal type window to and make your way through the server, but...whatever. Here's a screenshot of the rsh.


Comments
Post a Comment